Lync 2013 Reverse Proxy Configuration using IIS/ARR
In previous versions of Lync the Forefront Threat Management Gateway (TMG) was the Microsoft recommended and documented way of implementing the reverse proxy for Lync. Starting with 2013 TMG can no longer be licensed for use. It seems that the alternative to this is to use IIS/ARR to handle the reverse proxy.
The following directions outline how to configure and enable IIS/ARR on a windows server 2012(GUI) Standard Edition Server. *Please note that currently we had to use the GUI because you need to use the Web Platform Installer which is not supported in Server 2012 (core) configuration. We had tried to manually install the components and something in the Web Farm Framework 1.1 doesn't correctly get added.
The reverse proxy is required for things like mobile device connectivity, meeting presentations to external contacts and dial-in users.
Machine and Enviroment Specifications/Settings
- Server 2012 Standard Gui
- 2 NICs 1 external DMZ , 1 internal DMZ
- The default gateway should be on the external nic and if using OfficeWebApps servers to be able to present PowerPoint slides it will need 2 IP addresses in that external sub-net. In our example we will be using the following:
- x.x.36.84/32 will redirect to the Lync Front End Pool
- x.x.36.88/32 will redirect to the Office Web Apps Server
- The internal DMZ will need a single address with no default gateway. Instead you will need to manually add persistent routes to all internal networks that it will need to contact. Use a command similar to the following:
- route -p ADD 192.168.0.0 Mask 255.255.0.0 (NIC IP) if (NIC#)
- Add the following example DNS entries to outside DNS if using Split-Brain DNS based on the naming conventions you choose and purchased certificates for.
- dialin.company.com A record = x.x.36.84
- meet.company.com A record = x.x.36.84
- lyncdiscover.company.com A record = x.x.36.84
- lyncwebext.company.com A record = x.x.36.84
- lyncwebapps.company.com A record = x.x.36.88
- Add the all same DNS records from above to internal DNS as follows:
- If the record pointed to x.x.36.84 point it to a CNAME of the FQDN of your lync front end pool. For example, dialing.company.com CNAME record = lyncfepool1.local.company.com
- lyncwebsapps.company.com A record = (LyncWebApps Server FQDN) lyncwebapps.local.company.com
- Install Certificates that include all used DNS Subject Alternate names. To save in costs we used the same certificates used on the Lync edge server and included all SANS in that.
- Configure Firewall Rules according to Diagram 1.
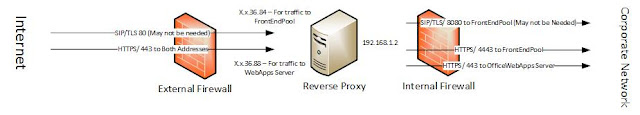 |
| Diagram 1 |
Installation and Configuration
To troubleshoot the configuration for officewebapps you can try and visit https://lyncwebapps.company.com/hosting/discovery. If successful, you should see XML output. If you are on an internal network, either change your test machines DNS servers or your host files to point to the external interfaces.
 This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.
This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.



