Tech at Mount
Technology observations of a system engineer, solution designer, and implementer.
Friday, December 19, 2014
Palo Alto Response pages and how they react using SSL/TLS
This link is a post to the palo alto document I created to outline response pages and what happens with SSL applications.
Friday, April 4, 2014
Setup a Read Only Active Directory Administrator in the Palo Alto
This document will
outline how to create an active directory administrator account on the device
that can log in and view reports and the
ACC.
This document will
not outline creating an LDAP, Kerberos, or RADIUS server profile which you will
require.
Step 1: Create an
authentication profile to allow the AD user to authenticate. This is done at
Device > Authentication Profile. Click add and in the allow list remove All
and add the users that you want to give read only permissions. Choose the
Authentication type and server profile to match the authentication type. You
also should change Login Attribute to sAMAccountName.
Step 2: Go to Admin
Roles in Device >Admin Roles. Add a new one disabling the features you don't
want the user to have access to. For our
example only the ACC and the features in the Monitor tab are left enabled everything
else is disabled.
Step 3: Go to
Administrators in Device > Administrators and create a new Administrator
account that keys off of the users defined in the Authentication Profile you
created. Choose the authentication
profile created then choose Role Based and the new Admin Role you created in
the Profile section.
Step 4: Commit
Step 5: Have the
user login with their Active Directory account.
Results: The user should now see limited actions and
only a few tabs. In our case ACC and Monitor at which point the user can see
any reports and information that they wish without having the ability to make
changes.
Friday, November 15, 2013
Sonicwall to Palo Alto Networks VPN Configuration
Sonicwall to Palo Alto Networks VPN configuration
Overview:
This document will outline the basic steps involved in establishing an IPSec Site to Site VPN tunnel between a Palo Alto Networks (PAN) and a Sonicwall. This document is also assuming the Sonicwall has a dynamic DHCP address it will be connecting from like you might have in a home or small office location.The Sonicwall device used is a TZ 170. The firmware versions used in the document are:
- PAN-OS version 5.0.8
- SonicOS Standard 3.1.2.6-97s
On the Palo Alto Device
- Navigate to the Network tab >IKE Gateways (click "new"):
- Enter the remote Gateway Name, local interface and IP, Choose Dynamic Peer Type since the peer has a DCHP address, otherwise you could enter a Peer Address, also enter a Pre-Shared Key that will match the other side. Since we are using a Dynamic peer you will need to enter a peer identification. Choose User FQDN(email address) and add an email address.
- You can leave the advanced Phase 1 options at there defaults.
- Go to the tab Networks > Interface > Tunnel and click Add on the bottom of the screen to create a new tunnel.
- Add an unused Tunnel id number, Assign it to a security zone, in this case the Trust zone and a virtual router.
- Go to the tab Networks > IPSec Tunnels and click add.
- On the general tab assign a tunnel name, choose the tunnel interface you created and choose the IKE Gateway you created from above.
- Click on the Proxy IDs tab. Click add and enter a Proxy ID name, a local IP netmask, the remote IP netmask and Any protocol.
- Go to the tab Network > Virtual Routers. On the general tab, add the Tunnel interface you create and ensure the used ethernet interfaces are added.
- Click on the Static Routes tab and add a static route for the remote network. Assign the remote network subnet and mask in destination. For interface choose the tunnel you created, and choose Next Hop of None.
- Go to Policies > Security and create the needed policy rules to setup the tunnels and then allow traffic through the tunnel.
- Commit the changes
On the Sonicwall
- Navigate to VPN > Settings
- Check the Enable VPN checkbox and add the Unique Firewall Identifier. Make the Unique firewall identifier be the User FQDN you used in the peer identifier on the Palo Alto.
- In the VPN Policies, Click Add to Create a new VPN policy.
- For the IPSec Keying Mode choose IKE using Preshared Secret, assign a name, assign the IPSec primary gateway Name or Address as the Palo Alto's interface, assign the matching shared secret.
- In the destination networks, we are assigning a specific network so only traffic headed to the assigned subnet will pass over the VPN.
- In the proposals tab, you want to choose aggressive exchange mode so this tried to initiate connections. All the other settings here need to match want you have in the IKE Crypto and IPSec Crypto sections of the Palo Alto. You need to check the Enable Perfect Forward Secrecy Box. I believe all the other settings are default matches on both sides.
- In the Advanced tab, check the box to Enable Keep Alive and ensure the VPN terminated option is set to LAN.
For additional troubleshooting see the following documents on the palo alto support site. https://live.paloaltonetworks.com/docs/DOC-1163
Labels:
IPsec,
Palo Alto Networks,
PAN-OS,
site-to-site,
Sonicwall,
VPN
Monday, April 1, 2013
No Ringback from PSTN to Lync via Audiocodes Gateway
Problem:
We had an issue where when calling a Lync phone from our PSTN with a Mediant 1000 Audiocodes device between Lync and the PSTN we were unable to hear ringback tones from the Lync device on the PSTN phone.Answer:
This problem is one of those issue were there was 1 drop down option that needed changed to resolve it.On the Audiocodes Gateway, go to Configuration > Full > SIP Definitions > General Parameters.
Go to the option Playback Tone to Tel and change it to Play Local Until Remote Media Arrives. Click Submit.
Monday, March 18, 2013
Lync 2013 Unable to receive SIP calls 503 Service Unavailable
In troubleshooting our Lync 2013 deployment, we were experiencing problems with the both sending and receiving calls to our Lync environment even though we believed we had voice routing and the gateway properly configured. In the OCS Logging logs and the gateway logs we were seeing the error SIP 2.0 / 503 Service Unavailable.
The resolution to the this issues was to add both the internal and external DNS entries for the FQDN of the Lync Edge pool. Making this change allowed Lync to be able to receive calls from both the legacy PBX and PSTN.
The resolution to the this issues was to add both the internal and external DNS entries for the FQDN of the Lync Edge pool. Making this change allowed Lync to be able to receive calls from both the legacy PBX and PSTN.
Friday, February 22, 2013
No Lync Call Park Application Service on Front End Server
During our Lync install we were trying to setup our Call Park in Lync 2013. This is configured in the administrative panel under Voice Features > Call Park. The basic setup is pretty simple but we were unable to get the FQDN of the destination server to populate.
 This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.
This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.
Problem: No call Park Application Service
Solution: Ensure that the enterprise voice feature is enabled in Topology Manager. Re-Publish the topography, then rerun deployment Wizard and Setup and Remove Lync Component Services. This will install the Call Park Service on server. Start up the service after it is installed and you can add it to your Call Park.
 This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.
This ended up being because the Call Park Application Service wasn't installed on the front end servers. Even though all other services were on the server and running. After some Googling and reading through the Microsoft Technet configuration articles, I ran into the solution.Problem: No call Park Application Service
Solution: Ensure that the enterprise voice feature is enabled in Topology Manager. Re-Publish the topography, then rerun deployment Wizard and Setup and Remove Lync Component Services. This will install the Call Park Service on server. Start up the service after it is installed and you can add it to your Call Park.
Tuesday, February 12, 2013
Lync 2013 Reverse Proxy Configuration using IIS/ARR
Lync 2013 Reverse Proxy Configuration using IIS/ARR
In previous versions of Lync the Forefront Threat Management Gateway (TMG) was the Microsoft recommended and documented way of implementing the reverse proxy for Lync. Starting with 2013 TMG can no longer be licensed for use. It seems that the alternative to this is to use IIS/ARR to handle the reverse proxy.The following directions outline how to configure and enable IIS/ARR on a windows server 2012(GUI) Standard Edition Server. *Please note that currently we had to use the GUI because you need to use the Web Platform Installer which is not supported in Server 2012 (core) configuration. We had tried to manually install the components and something in the Web Farm Framework 1.1 doesn't correctly get added.
The reverse proxy is required for things like mobile device connectivity, meeting presentations to external contacts and dial-in users.
Machine and Enviroment Specifications/Settings
- Server 2012 Standard Gui
- 2 NICs 1 external DMZ , 1 internal DMZ
- The default gateway should be on the external nic and if using OfficeWebApps servers to be able to present PowerPoint slides it will need 2 IP addresses in that external sub-net. In our example we will be using the following:
- x.x.36.84/32 will redirect to the Lync Front End Pool
- x.x.36.88/32 will redirect to the Office Web Apps Server
- The internal DMZ will need a single address with no default gateway. Instead you will need to manually add persistent routes to all internal networks that it will need to contact. Use a command similar to the following:
- route -p ADD 192.168.0.0 Mask 255.255.0.0 (NIC IP) if (NIC#)
- Add the following example DNS entries to outside DNS if using Split-Brain DNS based on the naming conventions you choose and purchased certificates for.
- dialin.company.com A record = x.x.36.84
- meet.company.com A record = x.x.36.84
- lyncdiscover.company.com A record = x.x.36.84
- lyncwebext.company.com A record = x.x.36.84
- lyncwebapps.company.com A record = x.x.36.88
- Add the all same DNS records from above to internal DNS as follows:
- If the record pointed to x.x.36.84 point it to a CNAME of the FQDN of your lync front end pool. For example, dialing.company.com CNAME record = lyncfepool1.local.company.com
- lyncwebsapps.company.com A record = (LyncWebApps Server FQDN) lyncwebapps.local.company.com
- Install Certificates that include all used DNS Subject Alternate names. To save in costs we used the same certificates used on the Lync edge server and included all SANS in that.
- Configure Firewall Rules according to Diagram 1.
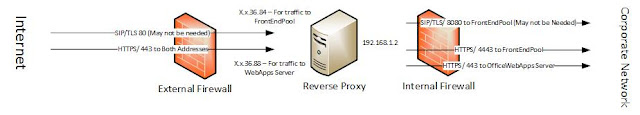 |
| Diagram 1 |
Installation and Configuration
- Open Server Manager > Dashboard
- Choose Add roles and features > Select your Server > Add the Web Server(IIS) role
- Open the IIS Server Manager from the search or Tools dropdown.
- Open the Microsoft Web Platform Components Installer or install it if needed then open it. (You may have to temporarily turn off the extended security features and change the trust zone of *.microsoft.com.
- Search for ARR
- Choose "Application Request Routing 2.5 with KB2589179."
- This will install several other dependent items you can see in the items to be installed including the following:
- IIS URL Rewrite Module 2
- Microsoft Application Request Routing 2.5
- Microsoft External Cache Version 1 for IIS 7
- Microsoft Web Farm Framework
After installation Re-open IIS Management Tools. You should now see a "Server Farms" option under the server connection as shown in Image 2.Image 2 - Create one empty folder to use as a physical path for the new websites for example "C:\inetpub\wwwroot\lync"
- Create 2 new websites. One for Front End Pool Services and One for Web Apps. Choose the folder created in the previous step for the Physical path. Bind both sites to HTTPS using the certificate containing SANs. Change the IP Address from :All Unassigned to the address according to what the site will proxy per above configuration. For Example, lyncWebExt site will be mapped to x.x.36.84. Leave the host name blank.
- Go to Server Farms and Create Server Farm.
- Create the LyncWebApps Farm by giving it a name
- At the Add Server screen add the full DNS name of officewebapps server. *Note this should match what you have in your Lync Topology Manager. In topology manager we used the lyncwebapps.company.com instead of the FQDN (lyncwebapps.private.domain.com) and ensure internal DNS is configured to reflect that.
- After you add the address you can expand that advanced settings and expand applicationRequestRouting. You can leave these settings to the default of 80 and 443 here.
- Click Finish
- Choose Yes to create the URL rewrite rule
- Open the Routing Rules feature under the farm you just created.
- Ensure both "Use URL Rewrite to inspect incoming requests" and "Enable SSL offloading" and checked
- On the right under Advanced Routing choose URL Rewrite
- Modify the pattern of the rule to match m/*
- Change the Scheme to HTTPS://
- Check to Stop processing of Subsequent Rules.
- Create a new rule and repeat the options above expect have it match the pattern of p/*. This will allow PowerPoint Presentations to work.
- Create a new LyncWebExt Farm and point it to you LyncFrontEnd pool FQDN.
- After you add the address you can expand that advanced settings and expand applicationRequestRouting. Change port 80 to port 8080 and change port 443 to 4443.
- Click Finish
- Choose Yes to have the rule created.
- In the Routing Rules > Advanced Routing > URL Rewrite
- Change the scheme to HTTPS://
- When finished your URL Rewrite should look like Image 3.
- Optional: For some additional security you can add a blank default HTML page to the default web site.
 |
| Image 3 |
Troubleshooting/Testing
To troubleshoot the configuration for officewebapps you can try and visit https://lyncwebapps.company.com/hosting/discovery. If successful, you should see XML output. If you are on an internal network, either change your test machines DNS servers or your host files to point to the external interfaces.
Labels:
ARR,
IIS,
Lync 2013 Enterprise Edition,
Reverse Proxy
Subscribe to:
Posts (Atom)

















