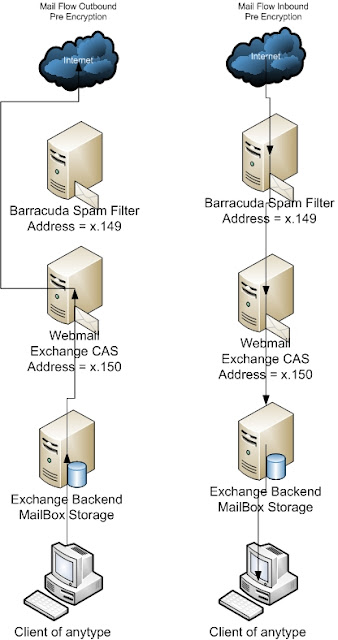
 |
| Image 1 - Pre Encryption mail flow |
Post Encryption Solutions - In our original implementation plans, we were looking at 2 separate reasons for encrypting of which PGP was the most obvious option. The 2 reasons were
- 1st the need for an email based encryption with a web based solution so that we could communicate securely with others who didn't have an encryption solution.
- 2nd was the need for disk encryption for our laptop clients. PGP would meet this need via providing both a universal gateway server, as well as desktop clients that can manage the disk encryption.
What we discovered - During the implementation and configuration we discovered a few things that changed our implementation plans to accommodate them.
- Our barracuda spam and virus firewall now supports acting as a web based encryption agent. You can filter based on content filtering rules in the barracuda just like in the PGP Universal Server. For example, we have a rule that any message flowing through the barracuda will encrypt messages containing [encrypt]. This is also possible in the universal server, but the PGP server is case sensitive while the barracuda is not.
- After trying to put the PGP server in mail flow between exchange and the barracuda we started having issues with backed up mail queues in exchange. The PGP system seems to have some rather strict limitations on messages per connection and rate control that there are no options to address to allow more messages
- A huge feature from our perspective was because the barracuda encryption service hosts the encrypted message in their cloud based system, in doing so; they provide the capabilities to allow users to self service password reset. From my discussion with our vendor this is a huge advantage because the PGP server requires administrators to reset user's passwords.
- As a benefit of having both the barracuda and PGP server and clients, we were able to come to a final deployment decision where the barracuda would do the web gateway encryption for the majority of campus. On select users that would require disk encryption, we would install the client because those users are also people who would find the value of client to client mail encryption.
 |
| Image 2 |
Post install - Here are the instructions of how it was done.
 |
| Exchange Smarthost to gateway example |
- In Exchange modify your Send Connector that forwards email to the internet. For us, it is Organization Configuration > Hub Transport > Send Connectors > Send to Internet. Usually this is the SMTP space that matches the address of *. In the network tab you need to configure it to send to the mail server doing the web based encryption, this can be either barracuda like in our case or simply the PGP gateway.
- To configure the PGP gateway, log into the web interface. Go to Mail > Proxies > then click on the SMTP Proxy. If the PGP server will be in the mail flow like option 3 above, you need to change the SMTP Proxy type to Unified. In the Outbound mail designated source IPs: add the IP address of your Exchange server. If the PGP server is your last mail flow stop before the Internet, choose Send mail directly to recipient mail server. If you have another outbound mail server like our barracuda, choose Send all outbound mail to relay and enter the IP of your next hop. For inbound mail enter the IP address of your exchange server in Mailserver hostname.
- In addition, if you are passing through the PGP server for inbound mail, you will need to configure Mail > Mail Routes and add your domain and Exchange server IP address. With the exception of policy setup, this should complete the configuration of the PGP Universal Server
- For the PGP policy setup you can modify the Outbound rule applicable to Server, Client under Mail > Mail Policy. We created a custom policy and placed it just prior to the Sign + Encrypt Buttons rule that is a default rule. You can see the rule setup in the image that would encrypt messages based on the subject containing [encrypt], a social security number, and a federal tax. In the actions, you want to encrypt on the recipient's key or send via Web Messenger, if using the PGP Web Messenger. If you are using something like the Barracuda to do encryption but you have the PGP server in the mail flow, you can set this to send unencrypted because it will be encrypted by the barracuda.
PGP encryption policy rule - If you also have a Barracuda to configure the outbound mail login to the web interface. Go to Basic > Outbound > Relay Using Trusted IP/Range, and add the IP address of either your PGP or Exchange server, whichever will be sending mail. This only enables outbound mail not the encryption portions.
- In the Barracuda, Go to Domains > Domain Manager > Manage Domain of your domain. In the Advanced > Encryption menu you can upload a custom image to appear in the emails.
- In the Barracuda, Go to Block/Accept > Content Filtering. Change the content filters to include something like a pattern of [\encrypt\] (which matches on [encrypt]), set Inbound Off, and Outbound to Encrypt, with Subject checked.
Best of luck with your install.

No comments:
Post a Comment